Securing Your Crypto in 2024: The Importance of OPSEC
Cryptocurrency has become an integral part of the global financial system, with millions of investors flocking to this decentralized world. However, as the industry grows, so do the risks. In 2023 alone, over $3.8 billion was stolen through cryptocurrency-related hacks and scams—a sharp rise from previous years. With hackers becoming more sophisticated, it's crucial to prioritize OPSEC (Operational Security) in 2024 to protect your assets.
The most common traps include phishing scams, malicious software, and social engineering attacks. Many users also fall victim to sophisticated SIM-swapping attacks and exploits targeting insecure crypto wallets and exchanges. It’s more important than ever to be vigilant and proactive in securing your digital wealth.
But how do you safeguard your cryptocurrency? This guide will help you understand the importance of OPSEC, compare secure devices, review the best exchanges and cold wallets, and highlight key tools for keeping your crypto safe.
The Role of 2FA in Strengthening Your OPSEC
One of the most effective ways to safeguard your digital assets is by enabling two-factor authentication (2FA) on every software, app, or account you use. 2FA adds an additional layer of security by requiring two forms of identification before granting access, making it significantly harder for hackers to compromise your accounts—even if they have your password.
Why 2FA Is Critical for Crypto Security
- Password Vulnerabilities: Passwords alone are often weak and can be cracked using brute force or stolen in data breaches. 2FA adds another layer that mitigates this risk.
- Protection Against Phishing: Even if a hacker tricks you into providing your login credentials through a phishing scam, they still can’t access your account without the second authentication factor.
- Mitigating SIM-Swapping Risks: By using app-based or hardware 2FA instead of SMS 2FA, you can drastically reduce the likelihood of a SIM-swap attack succeeding.
Types of 2FA and Best Practices
- App-Based 2FA
- Recommended Apps: Google Authenticator, Authy, and Microsoft Authenticator.
- How It Works: These apps generate time-based, one-time passwords (TOTP) that refresh every 30 seconds.
- Why It’s Better Than SMS: App-based 2FA operates independently of your phone number, making it immune to SIM-swapping attacks.
- Best Practice: Always back up your 2FA seeds securely to avoid losing access to your accounts.
- Hardware 2FA
- Devices: YubiKey and Titan Security Key.
- How It Works: A physical key is required to complete the login process, providing one of the most secure forms of 2FA.
- Why It’s Superior: Hardware 2FA ensures that even if a hacker has your password and phone, they cannot access your account without the physical key.
- Best Practice: Keep a backup hardware key in a secure location in case you lose the primary device.
- SMS 2FA
- How It Works: A code is sent via text message to your phone number.
- Why It’s Risky: Vulnerable to SIM-swapping attacks, making it the least secure 2FA option.
- When to Use: Only as a last resort if app-based or hardware 2FA isn’t available.
General 2FA Tips
- Review and Audit Accounts Regularly: Periodically check all accounts to ensure 2FA is enabled and functioning properly.
- Never Share 2FA Codes: Treat 2FA codes like your password—never share them with anyone, even if they claim to be tech support.
- Backup Recovery Codes: Store recovery codes securely, such as in a hardware wallet, encrypted USB drive, or secure offline location.
- Avoid Over-Reliance on SMS: Use app-based or hardware 2FA whenever possible to reduce vulnerabilities.
- Layer Security Measures: Use 2FA in conjunction with strong, unique passwords generated and stored by a password manager like 1Password or Apple’s iCloud Keychain.
By making 2FA a non-negotiable part of your OPSEC strategy, you significantly reduce the likelihood of unauthorized access to your accounts. Combine this with other security measures like cold wallets, secure browsing habits, and privacy-focused tools to stay one step ahead of potential threats.
Why iOS/macOS Devices Are Safer for Cryptocurrency Security
When it comes to choosing a device for managing your crypto, iOS and macOS stand out for their enhanced security features. These Apple platforms offer better protection compared to other operating systems due to several key factors:
- Sandboxing Principle: Apple devices implement an advanced sandboxing principle, isolating apps from one another and the system core. This limits the potential for malicious software to compromise the entire system or steal sensitive data, such as private keys or passwords.
- Frequent Security Updates: Apple maintains strict control over its ecosystem, regularly issuing security updates that patch vulnerabilities quickly. This ensures your device is less likely to be exploited by cybercriminals.
- Data Encryption: iOS and macOS devices automatically encrypt user data, making it harder for attackers to access personal or financial information. Even if the device is compromised, encrypted data provides another layer of defense.
- UNIX-based Architecture: Both iOS and macOS are built on a robust UNIX foundation, which enhances security through a well-established and secure architecture. This underlying structure is inherently resistant to common attack vectors due to its long-standing, battle-tested design.
- No Root Access for Users: Apple’s operating systems do not allow root access for regular users, making it much harder for attackers to gain full control of the device.
It’s important to note that other operating systems like Linux, Windows, or Android also offer strong security features, but their effectiveness largely depends on the user's security practices. macOS and iOS aren't necessarily safer than these platforms, but they make it easier for the average user to maintain security. With proper security hygiene—such as performing weekly check-ups, using virtual machines (VMs) to interact with potentially dangerous content, and staying vigilant—users of Linux, Windows, or Android can achieve similar levels of protection.
Best Exchanges for Crypto Security in 2024
While using exchanges for long-term storage of your crypto is not advisable, they are necessary for buying and selling. To minimize risk, it’s crucial to choose an exchange with a strong reputation for security. Here are some of the best exchanges with top-notch safety measures:
- Coinbase: As one of the most well-regulated and trusted exchanges globally, Coinbase employs multi-layered security measures. These include insurance for stored assets, biometric logins, and cold wallet storage. It also offers strong two-factor authentication (2FA) features. Coinbase is also the issuer of the first U.S.-approved Bitcoin ETF, giving it strong regulatory oversight and security but with a slightly less streamlined user experience compared to other exchanges like Binance.
- Kraken: Known for its rigorous security protocols, Kraken is another top exchange. It uses full reserves, meaning your crypto is not loaned out or reinvested. Kraken also offers encrypted cold storage and advanced options for two-factor authentication. Its transparency and focus on security make it a reliable choice for serious traders.
- Binance: Binance has a massive global presence and offers features like withdrawal address whitelisting, hardware-based 2FA, and cold wallet storage for most assets. However, Binance has faced compliance issues in several countries, raising some regulatory concerns. Despite these challenges, its user interface and trading features are considered superior to many other platforms, making it a popular choice for frequent traders.
- Bitfinex: Popular among whales (large-scale traders), Bitfinex offers advanced trading tools, deep liquidity, and strong security measures like cold storage and 2FA. Its robust infrastructure and usage by institutional traders make it a go-to platform for serious market participants, though it may be more suited to experienced users.
Disclaimer: While these exchanges have excellent security measures, they should only be used as on/off ramps for buying and selling. Never store large amounts of cryptocurrency on an exchange long-term—always move it to a cold wallet for maximum safety.
Best Cold Wallets: Ledger vs. Tangem
Using a cold wallet is one of the most effective ways to secure your cryptocurrency. Cold wallets store your private keys offline, away from internet-connected devices, making it nearly impossible for hackers to gain access. Let’s compare two of the top options:
- Ledger: Ledger has been a top player in the hardware wallet space for years. Its Nano S Plus and Nano X devices are widely used, offering multi-currency support, secure chip technology, and integration with the Ledger Live app. Ledger is highly reliable, but it has faced some controversy in recent years due to a data breach involving user information (although the breach did not affect wallet security).
- Tangem: Tangem is an emerging player in the cold wallet market, gaining popularity for its innovative approach. Tangem cards function as a tap-to-pay card with no screen or battery. It is also a Swiss-regulated company, which adds another layer of trust and compliance. Here’s why Tangem is better in some areas:
- Superior Convenience: Tangem’s card form factor is more durable and easier to use than traditional hardware wallets.
- Multi-Signature Support: Tangem offers robust multi-signature wallet features, increasing security by requiring multiple devices to sign transactions.
- No Online Firmware Updates: Unlike Ledger, which requires online firmware updates that could expose vulnerabilities, Tangem’s security model eliminates this need, reducing risk.
Using Cold Wallets Properly:
To maximize cold wallet security, ensure the following:
- Always buy directly from the manufacturer to avoid tampered devices.
- Keep the seed phrase (the 12-24 word recovery phrase) offline and in a secure location. Never store it digitally.
- Do not save your seed phrase as a photo in your gallery. Malicious programs can run scripts that check for such patterns and compromise your security.
- Test small transactions before transferring large amounts.
- Enable multi-signature security if available.
OPSEC Applications: Enhancing Your Digital Security
OPSEC isn’t just about securing your wallet—it’s about securing your entire digital life. To ensure maximum privacy and security, use specialized tools designed for enhanced protection.
- Black.com for Secure Emails: While ProtonMail has gained a strong reputation for secure communication, Black.com is an even better choice in 2024. Black.com offers end-to-end encryption, full metadata stripping, and a strict zero-logging policy. It’s ideal for those who want absolute privacy in email communications, even from the service provider itself.
- Signal: Signal remains the gold standard for secure messaging. It offers end-to-end encryption, ensuring your messages can only be read by the intended recipient, with no intermediaries able to access the content.
- Mullvad VPN: For private browsing and secure connections, Mullvad VPN stands out with several impressive features. It offers strong encryption, a no-logs policy, and an anonymous account creation process. Mullvad doesn’t require personal information for sign-up—you simply generate an account number and can pay with cryptocurrency, preserving your anonymity. Additionally, Mullvad has a transparent security policy and allows users to connect via WireGuard or OpenVPN for secure tunneling.
- Apple Passkeys and Passwords: Apple’s password management system is an excellent choice for 2024, offering seamless integration across macOS and iOS devices. Apple Passkeys are particularly powerful because they eliminate the need for traditional passwords, using Face ID or Touch ID to log in securely. This reduces the risk of phishing attacks and password leaks, making it a more secure option than traditional password managers. Apple’s iCloud Keychain securely stores your passwords and generates strong, unique passwords for every account, ensuring that all data is encrypted end-to-end.
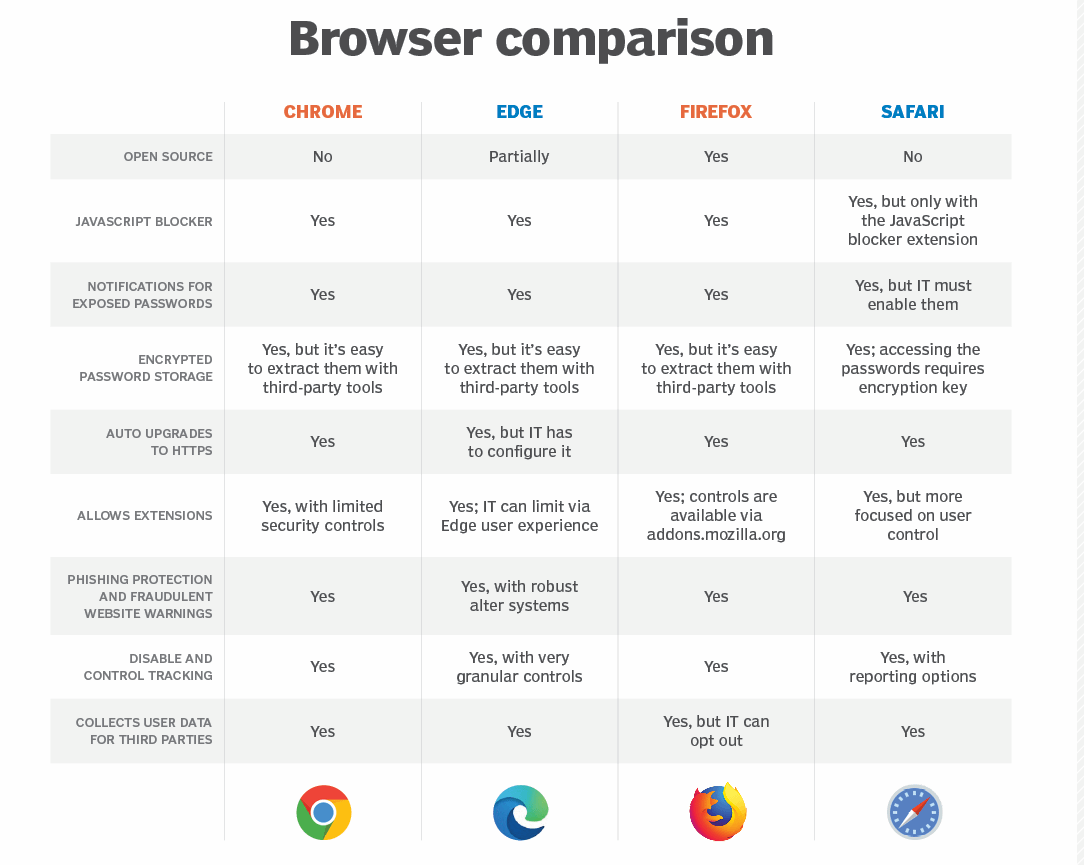
Beware of Browser Risks: Why Chrome Isn’t Your Best Option for Security
A significant number of security breaches happen through vulnerabilities in web browsers, and while Chrome is popular, it is not the most secure choice for cryptocurrency transactions. Here’s why and how to stay safer:
- Data Collection: Chrome, as a Google product, is deeply integrated into Google’s data-collection ecosystem. While it offers robust security features, it also tracks your browsing habits, which can expose sensitive information and make you more vulnerable to targeted attacks.
- Extensions and Malware: Chrome’s vast extension library is both a strength and a weakness. Malicious extensions or compromised updates can be exploited by hackers to access your sensitive data, including passwords and crypto keys.
Safer Browsing Practices:
- Use a Privacy-Focused Browser: Switch to browsers like Brave or Firefox. Brave, for example, blocks ads and trackers by default, reducing your exposure to malicious content and phishing attempts. Firefox, with its strong security features and privacy extensions, is another solid choice.
- Use a VPN: Whenever accessing crypto exchanges or wallets, always use a reliable VPN like Mullvad, NordVPN, or ExpressVPN. This encrypts your connection, preventing man-in-the-middle attacks and masking your IP address from hackers.
- Disable Third-Party Cookies and Trackers: Enable the Strict Tracking Protection mode in browsers like Firefox or Brave. This will block cross-site trackers that can harvest information about your browsing habits.
- Avoid Browser-Based Wallets: Many users rely on browser extensions like MetaMask for interacting with decentralized finance (DeFi) apps. While useful, these wallets can be targets for phishing attacks. Instead, use hardware wallets or dedicated desktop applications to minimize risks.
- Regularly Update Your Browser: Always ensure your browser is up-to-date. Most security vulnerabilities are exploited because users run outdated versions of their browsers, which lack the latest security patches.
By following these practices and combining them with secure applications, you’ll greatly reduce your risk of being exposed to crypto hacks and scams.
-LT
